I will tell you about the favorite operating system of real hackers. Everything is exactly like in spy films!
2009 saw a modest revolution in the OS world. You probably haven't heard of it, but the guys from that same Tor Project released their own operating system, codenamed TAILS (The Amnesic Incognito Live System). She gained her fame mainly thanks to Edward Snowden, who was her active user at the time of the NSA data leak. Today we will analyze what is cool about it and why it is generally needed.

Tails is not a classic OS. The most important thing you need to know is that "tails" are launched directly from the USB stick. As for me, this is very cool and I immediately remember the scenes of hacking over computers from some Hollywood blockbusters. As for the base, this is Linux itself, and for those who fumble with the GNU / Linux distribution based on Debian and the granddaughter of Incognito OS, too.
But this is all a waste of time. We are interested in what this baby can do. Let's go straight to the key features. When launched from a flash drive, Tails works exclusively in RAM, which means it leaves no traces of its activities. That is, as soon as you shut down the computer, or pulled out the USB flash drive, all OS files disappear from the RAM, which opens up a whole field of new spy capabilities. Further, the OS automatically replaces the Mac-address of the device + the entire Internet connection is via TOR. As for the secondary, in Tails, of course, the most necessary hacker utilities are preinstalled, such as Internet traffic analyzers for the same WiFi hack. Well, and where without the basic functions. It has its own cut-down photo / video editors, Chinese paints, fake Word, and more. In short, everything you need for normal work is available.
How to install?
First you need to get at least an 8 GB flash drive. Then you will need a program to transfer the OS image to a USB flash drive, for example Etcher. Then we import the whole thing into the desired PC and install it. Then there is nothing complicated, MAC settings, password setting and so on. The most important thing to remember is the Persistent Volume setting. This is the function of saving any files, since after each shutdown, the entire history of the OS is reset. I will not sign about it, you will find guides on the Internet. Just pay attention to it.
Download the OS itself here:

Outcome
So, we give a verdict to our tailed friend. The thing is cool and even despite its age, relevant, as it is regularly updated. This OS is undoubtedly one of the most secure in terms of information confidentiality, but nuances can arise with anonymity.
[IMG alt="Lord777"]https://carder.market/data/avatars/m/125/125495.jpg?1685977674[/IMG]
SHOCK! Tails shit but we found her! New Best OS!
Introduction
Hello <$ friend>, in this article I would like to introduce you to one of the most powerful anonymization tools. Before reading this article, you will have to make sure you have two hands and one brain - you will need them.
Now I'll tell you why Tails is not a panacea. How the FSB and other special services from three letters calculate the attackers using Tor (of course, we will also talk about the shortcomings of the Tor network and its analogues, but in another article). And as the cherry on top, I will point you to the most powerful VPN-Tor-VPN bundle that will protect you from any "timing" attacks.
Tails - the myth of security

You are probably already familiar with TailsOS, but I hasten to disappoint you. Many call this OS the most secure and recommend actively using it, because Uncle Snowden himself used Tails, and he, like no one else, knows the price of anonymity. Based on the article on WLAN, you should have already understood that in the world of anonymity and information security, nothing is as easy as it seems to you, here is the same situation.
Let's go from afar, you know that Tails has already been hacked? Facebook worked with the FBI and a third-party contractor to develop a 0-day exploit for Tails. So they figured out the real IP of Buster Hernandez, the famous American pervert. Of course, 0-day for that and 0-day that they do not know about it. Although, according to the Tails team, this bug has already been fixed, I just wanted to dispel the myth about Tails being absolutely safe ..
Hint # 1:
0-day are the most valuable types of vulnerabilities. Their very name fully reveals the essence, these are errors that were found literally on the same day, therefore there are no remedies against them at the moment.
How will the feds find you through Tor?
Let's abstract from the control of input and output nodes, 0-day exploits and other rubbish, okay? Your bulbs are too complicated for Comrade Major, you know? Moreover, why hack the Tor network, which is quite difficult if you can just ask the provider? You know that in our country it is not customary to refuse people in uniform. Why am I doing this? I want to tell you about timing attacks, which are an effective means of deanonymizing Tor users.
Tor packets are easily recognized by the provider, the matter is in a specific byte sequence and frequent IP changes. This means that the provider sees all the actions that you perform on this network, with one caveat. Tor traffic is encrypted, so the ISP doesn't know what exactly you were doing on the network, but the major doesn't need it. Let's say an officer knows the dates and approximate times when you entered Tor (these can be records of logins in networks, for example, or data on visits to different sites). Let's say we can narrow the circle of suspects within the country, but in reality, the circle usually narrows down to one specific region, for example, Moscow and its region. Immediately after that, data on the use of Tor traffic is requested from all local providers.
Then the major will wait for your next login. New clients will appear, but the major will look at those that were at the first login to the network, and some of them will be eliminated. Gradually, the loop will narrow until it is on your neck, the action can be repeated dozens of times. But the provider knows everything about you, down to what kind of porn you prefer, including the address, so it will calmly send the investigation team from feds directly to your home.
How to avoid timing attacks? Whonix
You cannot use Tor and VPN on the same machine, but you can start the VPN-Tor chain by running your Tails on the same virtual machine. Then the provider will see completely white traffic, which will not interest the major. But the very transfer of Tails to a virtual machine makes this OS not the most convenient tool in comparison with the same Whonix. Whonix is a distribution originally designed for virtualization, which gives us a unique opportunity - to create a VPN-Tor-VPN chain (this can be done with Tails using the same gateway, but this is a crutch). Thus, Whonix is a much more anonymous operating system than Tails, especially since Whonix infection does not threaten your data in any way, but Tails infection is a problem.
You see, the creators claim that Tails is a forgetful OS, but it all depends on our actions. Often, Tails users leave persistence directories that store whatever software they don't want to reinstall after Tails' amnesia attacks. But the backdoor can fit into these sections too ..? On the other hand, such amnesia can be easily repeated in any other distribution, simply by running it in live mode, and on a virtual machine it will be enough to reset it from time to time.
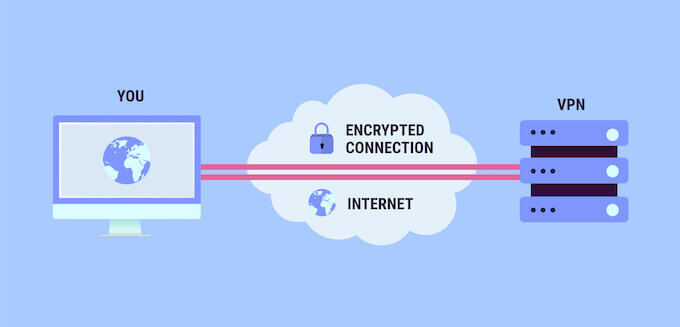
As you might have guessed, for this scheme you will need a VPN client. Anyone will do, but I prefer paid customers who didn't pay us to advertise ... It's not that I have extra money, but that a free VPN loves to leak user data. In addition, by offering a very low speed, which is critical for us, because our chain significantly reduces the speed. Add to this the restrictions from free VPN.
Installing Whonix
When you go to the installation site, you will be prompted to select the platform you will run Whonix on. Choose VirtualBox without a twinge of conscience. Then you have to choose between "Whonix with XFCE" and "Whonix with CLI". In fact, they suggest choosing a version with and without a graphical environment, which is the best option, because a computer is less expensive in terms of resources. But it's better not to put CLI if you think that Linux is the command line (just kidding, it's better not to install CLI at all. This is not rational in our case, because you still have to set up a graphical environment for your daily tasks. We are not setting up a server In general, we have something to talk about here, but this is not the topic of our article).
Installation:
After installation, we will be given a ready-made .ova, there is no need to strain at all. As a result, we will get 2 virtual machines named "Gateway" and "Workstation", which are responsible for traffic transmission and user work, respectively.
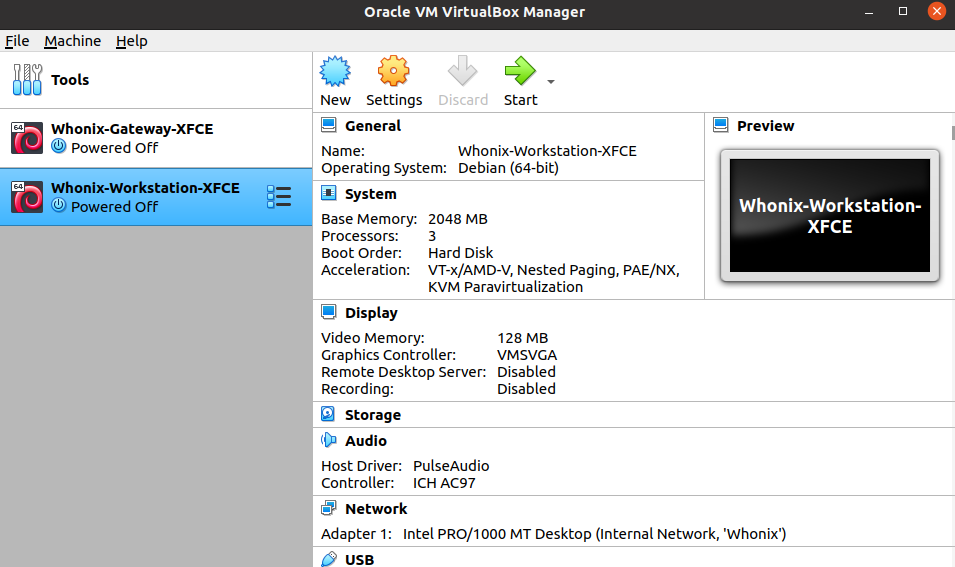
Before launching Whonix, let's launch the VPN (I hope you can handle this yourself). And in general, take it as a habit: first VPN, then Whonix. Then we launch Workstation and Gateway. We will be prompted to agree to the rules at the first launch, which is what we do. The XFCE version of Gateway will offer us graphical customization. In general, it is performed by bluntly clicking the "Next" button, but if something does not suit us, then the configuration section is available, where you can, for example, configure bridges. But first, you should change the user passwords (the default password is changeme):
Code:
sudo passwd <username>
Next, let's launch VPN on Workstation using the openvpn client and configuration for it (all normal VPN services offer openvpn configurations. Most likely, you can find one in your personal account and install it on Whonix) use the openvpn client, which you have to install first.
Installation:
Code:
sudo apt install openvpn
Usage:
Code:
sudo openvpn <config file>
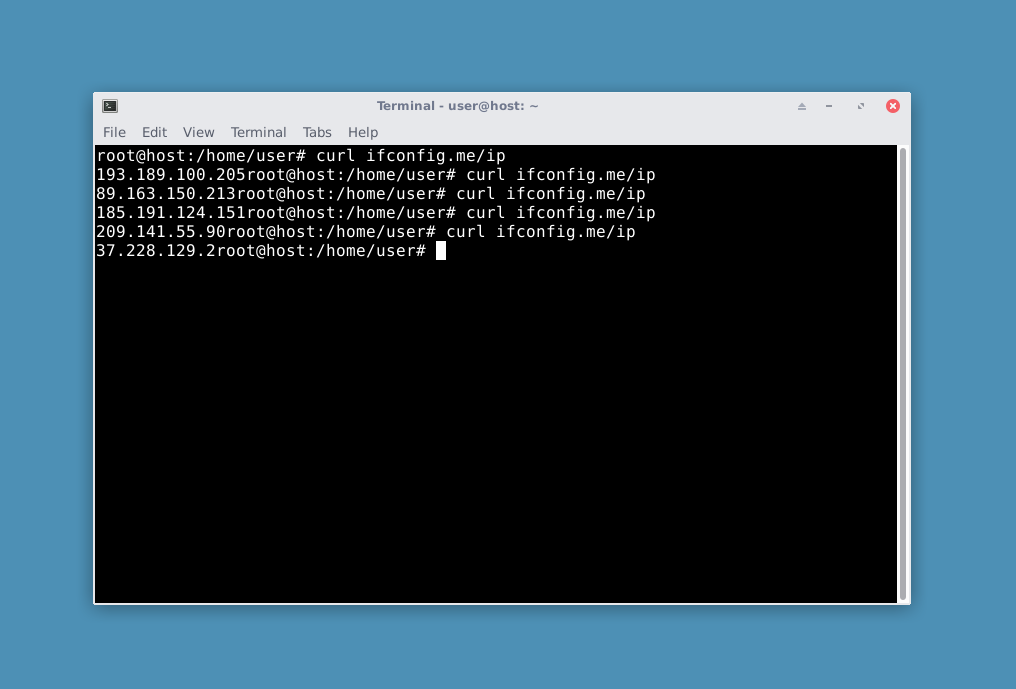
Congratulations, we were able to launch VPN-Tor-VPN (just VPN-Tor on the screen)
Summary
To summarize this article, we've dispelled the Tails security myth, and you've been introduced to (or at least launched) a wonderful virtual machine OS like Whonix.
But remember that there is no panacea in anonymity and security. Each tool is optimal for its task. For example, Whonix is quite cumbersome to deploy, but provides more flexible configuration, better anonymization and protection tools with more flexible configuration. At the same time, Tails can fit in your pocket (Whonix also has live versions on USB, but this is not entirely advisable) and does not require any special skills.
2009 saw a modest revolution in the OS world. You probably haven't heard of it, but the guys from that same Tor Project released their own operating system, codenamed TAILS (The Amnesic Incognito Live System). She gained her fame mainly thanks to Edward Snowden, who was her active user at the time of the NSA data leak. Today we will analyze what is cool about it and why it is generally needed.

Tails is not a classic OS. The most important thing you need to know is that "tails" are launched directly from the USB stick. As for me, this is very cool and I immediately remember the scenes of hacking over computers from some Hollywood blockbusters. As for the base, this is Linux itself, and for those who fumble with the GNU / Linux distribution based on Debian and the granddaughter of Incognito OS, too.

But this is all a waste of time. We are interested in what this baby can do. Let's go straight to the key features. When launched from a flash drive, Tails works exclusively in RAM, which means it leaves no traces of its activities. That is, as soon as you shut down the computer, or pulled out the USB flash drive, all OS files disappear from the RAM, which opens up a whole field of new spy capabilities. Further, the OS automatically replaces the Mac-address of the device + the entire Internet connection is via TOR. As for the secondary, in Tails, of course, the most necessary hacker utilities are preinstalled, such as Internet traffic analyzers for the same WiFi hack. Well, and where without the basic functions. It has its own cut-down photo / video editors, Chinese paints, fake Word, and more. In short, everything you need for normal work is available.
How to install?
First you need to get at least an 8 GB flash drive. Then you will need a program to transfer the OS image to a USB flash drive, for example Etcher. Then we import the whole thing into the desired PC and install it. Then there is nothing complicated, MAC settings, password setting and so on. The most important thing to remember is the Persistent Volume setting. This is the function of saving any files, since after each shutdown, the entire history of the OS is reset. I will not sign about it, you will find guides on the Internet. Just pay attention to it.

Download the OS itself here:
You do not have permission to view link
Log in or register now.

Outcome
So, we give a verdict to our tailed friend. The thing is cool and even despite its age, relevant, as it is regularly updated. This OS is undoubtedly one of the most secure in terms of information confidentiality, but nuances can arise with anonymity.
You do not have permission to view link
Log in or register now.
[IMG alt="Lord777"]https://carder.market/data/avatars/m/125/125495.jpg?1685977674[/IMG]
Lord777
Professional
Messages2,089Reputation
You do not have permission to view link
Log in or register now.
Reaction score1,143Points113-
You do not have permission to view link Log in or register now.
-
You do not have permission to view link Log in or register now.
SHOCK! Tails shit but we found her! New Best OS!
Introduction
Hello <$ friend>, in this article I would like to introduce you to one of the most powerful anonymization tools. Before reading this article, you will have to make sure you have two hands and one brain - you will need them.
Now I'll tell you why Tails is not a panacea. How the FSB and other special services from three letters calculate the attackers using Tor (of course, we will also talk about the shortcomings of the Tor network and its analogues, but in another article). And as the cherry on top, I will point you to the most powerful VPN-Tor-VPN bundle that will protect you from any "timing" attacks.
Tails - the myth of security

You are probably already familiar with TailsOS, but I hasten to disappoint you. Many call this OS the most secure and recommend actively using it, because Uncle Snowden himself used Tails, and he, like no one else, knows the price of anonymity. Based on the article on WLAN, you should have already understood that in the world of anonymity and information security, nothing is as easy as it seems to you, here is the same situation.
Let's go from afar, you know that Tails has already been hacked? Facebook worked with the FBI and a third-party contractor to develop a 0-day exploit for Tails. So they figured out the real IP of Buster Hernandez, the famous American pervert. Of course, 0-day for that and 0-day that they do not know about it. Although, according to the Tails team, this bug has already been fixed, I just wanted to dispel the myth about Tails being absolutely safe ..
Hint # 1:
0-day are the most valuable types of vulnerabilities. Their very name fully reveals the essence, these are errors that were found literally on the same day, therefore there are no remedies against them at the moment.
How will the feds find you through Tor?

Let's abstract from the control of input and output nodes, 0-day exploits and other rubbish, okay? Your bulbs are too complicated for Comrade Major, you know? Moreover, why hack the Tor network, which is quite difficult if you can just ask the provider? You know that in our country it is not customary to refuse people in uniform. Why am I doing this? I want to tell you about timing attacks, which are an effective means of deanonymizing Tor users.
Tor packets are easily recognized by the provider, the matter is in a specific byte sequence and frequent IP changes. This means that the provider sees all the actions that you perform on this network, with one caveat. Tor traffic is encrypted, so the ISP doesn't know what exactly you were doing on the network, but the major doesn't need it. Let's say an officer knows the dates and approximate times when you entered Tor (these can be records of logins in networks, for example, or data on visits to different sites). Let's say we can narrow the circle of suspects within the country, but in reality, the circle usually narrows down to one specific region, for example, Moscow and its region. Immediately after that, data on the use of Tor traffic is requested from all local providers.
Then the major will wait for your next login. New clients will appear, but the major will look at those that were at the first login to the network, and some of them will be eliminated. Gradually, the loop will narrow until it is on your neck, the action can be repeated dozens of times. But the provider knows everything about you, down to what kind of porn you prefer, including the address, so it will calmly send the investigation team from feds directly to your home.
How to avoid timing attacks? Whonix
You cannot use Tor and VPN on the same machine, but you can start the VPN-Tor chain by running your Tails on the same virtual machine. Then the provider will see completely white traffic, which will not interest the major. But the very transfer of Tails to a virtual machine makes this OS not the most convenient tool in comparison with the same Whonix. Whonix is a distribution originally designed for virtualization, which gives us a unique opportunity - to create a VPN-Tor-VPN chain (this can be done with Tails using the same gateway, but this is a crutch). Thus, Whonix is a much more anonymous operating system than Tails, especially since Whonix infection does not threaten your data in any way, but Tails infection is a problem.
You see, the creators claim that Tails is a forgetful OS, but it all depends on our actions. Often, Tails users leave persistence directories that store whatever software they don't want to reinstall after Tails' amnesia attacks. But the backdoor can fit into these sections too ..? On the other hand, such amnesia can be easily repeated in any other distribution, simply by running it in live mode, and on a virtual machine it will be enough to reset it from time to time.

As you might have guessed, for this scheme you will need a VPN client. Anyone will do, but I prefer paid customers who didn't pay us to advertise ... It's not that I have extra money, but that a free VPN loves to leak user data. In addition, by offering a very low speed, which is critical for us, because our chain significantly reduces the speed. Add to this the restrictions from free VPN.
Installing Whonix
When you go to the installation site, you will be prompted to select the platform you will run Whonix on. Choose VirtualBox without a twinge of conscience. Then you have to choose between "Whonix with XFCE" and "Whonix with CLI". In fact, they suggest choosing a version with and without a graphical environment, which is the best option, because a computer is less expensive in terms of resources. But it's better not to put CLI if you think that Linux is the command line (just kidding, it's better not to install CLI at all. This is not rational in our case, because you still have to set up a graphical environment for your daily tasks. We are not setting up a server In general, we have something to talk about here, but this is not the topic of our article).
Installation:
You do not have permission to view link
Log in or register now.
After installation, we will be given a ready-made .ova, there is no need to strain at all. As a result, we will get 2 virtual machines named "Gateway" and "Workstation", which are responsible for traffic transmission and user work, respectively.

Before launching Whonix, let's launch the VPN (I hope you can handle this yourself). And in general, take it as a habit: first VPN, then Whonix. Then we launch Workstation and Gateway. We will be prompted to agree to the rules at the first launch, which is what we do. The XFCE version of Gateway will offer us graphical customization. In general, it is performed by bluntly clicking the "Next" button, but if something does not suit us, then the configuration section is available, where you can, for example, configure bridges. But first, you should change the user passwords (the default password is changeme):
Code:
sudo passwd <username>
Next, let's launch VPN on Workstation using the openvpn client and configuration for it (all normal VPN services offer openvpn configurations. Most likely, you can find one in your personal account and install it on Whonix) use the openvpn client, which you have to install first.
Installation:
Code:
sudo apt install openvpn
Usage:
Code:
sudo openvpn <config file>

Congratulations, we were able to launch VPN-Tor-VPN (just VPN-Tor on the screen)
Summary
To summarize this article, we've dispelled the Tails security myth, and you've been introduced to (or at least launched) a wonderful virtual machine OS like Whonix.
But remember that there is no panacea in anonymity and security. Each tool is optimal for its task. For example, Whonix is quite cumbersome to deploy, but provides more flexible configuration, better anonymization and protection tools with more flexible configuration. At the same time, Tails can fit in your pocket (Whonix also has live versions on USB, but this is not entirely advisable) and does not require any special skills.