Member
- Joined
- Oct 14, 2023
- Messages
- 225
- Thread Author
- #1
How do the 3 most reliable methods of stealing data from inattentive victims work?
According to statistics from the information security company ANY.RUN, in 2023, the use of QR codes, CAPTCHAS, and steganography became a popular phishing method.
One of the new phishing techniques - Quishing (QR and phishing), involves hiding malicious links in QR codes. This method avoids detection by traditional anti-spam filters focused on text messages. Many security tools are not able to decipher the contents of QR codes, which makes the method particularly effective for cybercriminals.
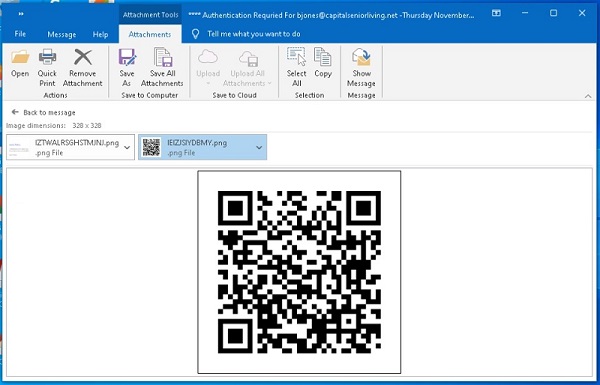
Malicious QR code in an email
Phishing attacks also use CAPTCHA, a website security tool. Criminals use CAPTCHAS to mask forms of credential collection on fake sites by creating hundreds of domain names using the Randomized Domain Generated Algorithm (RDGA) and implementing CAPTCHAS. For example, in an attack on a Halliburton Corporation employee, the victim is first asked to complete a CAPTCHA check, and then redirected to a fake Office 365 login page.
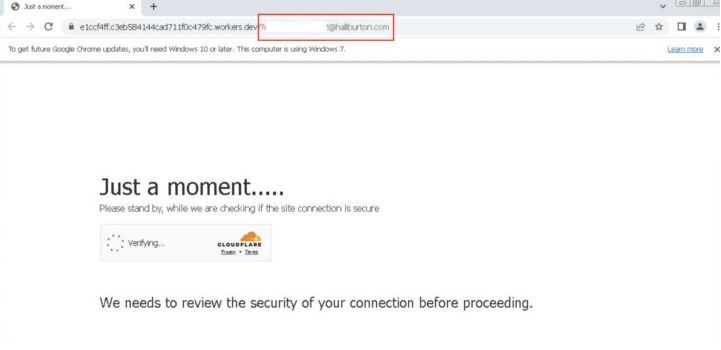
Passing a CAPTCHA on a phishing site
Phishing campaigns also use steganography, a method of hiding data in various media. For example, in a fake email from a Colombian government organization that contains a link to a file on Dropbox, a hidden VBS script extracts an image with malicious code when executed, infecting the victim's system.
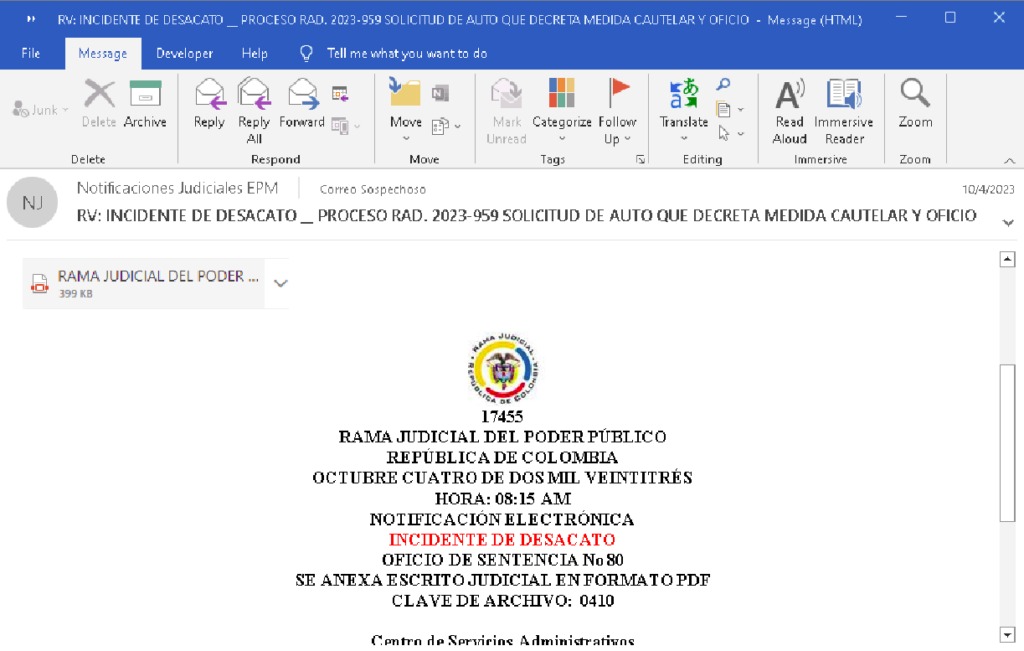
Malicious code is hidden in the document's logo
With the evolution of phishing attacks and new techniques such as QR codes, captchas, and steganography, users and organizations need to be more alert and aware of potential threats. It is important to use modern tools and services to analyze and prevent malicious attacks. Cybersecurity training and awareness also play a key role in combating cybercrime.
According to statistics from the information security company ANY.RUN, in 2023, the use of QR codes, CAPTCHAS, and steganography became a popular phishing method.
One of the new phishing techniques - Quishing (QR and phishing), involves hiding malicious links in QR codes. This method avoids detection by traditional anti-spam filters focused on text messages. Many security tools are not able to decipher the contents of QR codes, which makes the method particularly effective for cybercriminals.

Malicious QR code in an email
Phishing attacks also use CAPTCHA, a website security tool. Criminals use CAPTCHAS to mask forms of credential collection on fake sites by creating hundreds of domain names using the Randomized Domain Generated Algorithm (RDGA) and implementing CAPTCHAS. For example, in an attack on a Halliburton Corporation employee, the victim is first asked to complete a CAPTCHA check, and then redirected to a fake Office 365 login page.

Passing a CAPTCHA on a phishing site
Phishing campaigns also use steganography, a method of hiding data in various media. For example, in a fake email from a Colombian government organization that contains a link to a file on Dropbox, a hidden VBS script extracts an image with malicious code when executed, infecting the victim's system.

Malicious code is hidden in the document's logo
With the evolution of phishing attacks and new techniques such as QR codes, captchas, and steganography, users and organizations need to be more alert and aware of potential threats. It is important to use modern tools and services to analyze and prevent malicious attacks. Cybersecurity training and awareness also play a key role in combating cybercrime.